Brain Melt
Have fun and find the flag :)
Challenge
TL;DR: Extract
.pycfrom executable usingpyinstxtractor, and decompilepycusingpycdc.
By running strings on the executable, we can see strings of python indicating that this is likely a PyInstaller file.
zPYZ-00.pyz
'python39.dll
First, we extract the compiled python bytecodes using PyInstaller Extractor.
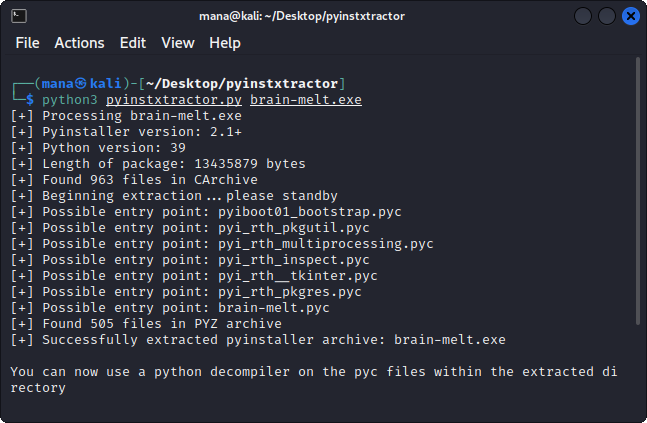
Next, as Python 3.9 is used for this executable, the standard decompyle6 would not work and we will have to use Decompyle++ to decompile the bytecodes. The decompiled source code we get from decompiling brain-melt.pyc can be seen here.
The flag seems to be obfuscated and can be decrypted and can be printed out using the decrypt and deobfuscate functions. Just print the result from these functions to get the flag.
import base64
def decrypt(s1, s2):
return ''.join((lambda x: [ chr(ord(c1) ^ ord(c2)) for c1, c2 in x ])(zip(s1, s2)))
def deobfuscate():
part1 = '2ec7627d{galf'[::-1]
part2 = str(base64.b64decode('NjIwM2I1Y2M2OWY0'.encode('ascii')), 'UTF8')
part3 = decrypt('\x17*\x07`BC\x14*R@\x14^*', 'uKeVuzwIexplW')
key = part1 + part2 + part3
return key
print(deobfuscate())
Flag: flag{d7267ce26203b5cc69f4bab679cc78d2}